http://www.bgpexpert.com/bgpanswers.php
Glossary
- AS: Autonomous System. A large network or group of networks that share a common a unified routing policy.
- ASN: An Autonomous System Number. A unique, unsigned, 16 or 32 bit numbers that identify an individual AS.
- BGP: Border Gateway Protocol: protocol for exchanging routing information between gateway hosts (each with its own router) in a network of autonomous systems. MOST BASIC DEFINITION: Is it the routing protocol that makes the Internet work.
- Unlike all other routing protocols, BGP uses TCP as its transport protocol.
- Widely accepted as the most complex and difficult to configure Internet Protocol.
- Exterior gateway protocol for exchanging routing and reachability information among autonomous systems on the Internet. Path vector protocol, or distance-vector routing protocol.
- As of 2016-01-18 version 4 is the current and pretty much only supported protocol.
- A layer 4 protocol that sits on top of TCP
- The routing table contains:
- A list of known routers
- The addresses that they can reach
- The cost metric associated with the path to each router so that best available route is chosen.
- ONLY the affected part of routing table is sent to peers
- Usually exchange between competing business entities on the open public Internet.
- It is not simply the best path but provides the ability to configure to include the reality of peering and business agreements.
- AS Path: Autonomous Systems Path. The path between ASes that data traverses to get to a specific router. BGP uses AS Path for loop detection and best path selection.
- TDM: time-division multiplex
- TDMA: time-division multiple access
- Half Duplex: Provides bi-directional communication, but only one direction at a time.
- Full Duplex: Provided concurrent bi-directional communication, radios: transmit on one frequency and receive on another. Ethernet connections use two pairs of wires for outbound data, and two pairs of wires for inbound data, making the cable a collision free environment.
- RIP: Routing Information Protocol, an older routing protocol to determine distances between routers.
- RIB: Routing Information Base. Contains multiple paths to a given destination. Keeps track of routes that could possibly be used.
- *MED: Multi-exit Discriminator: Makes it possible, via BGP, to tell a remote AS that if there are multiple exit points on to your network, a specific exit point is preferred.
- OSPF: open shortest path first is a routing protocol for IP networks that falls into the group of interior routing protocols. That means that it distributes routing information between routers that are a part of the same AS.
- IGPs: Interior Gateway Protocols (RIP, OSPF, IGRP, EIGRP, IS-IS) are used within the network of a single organization
- EGPs: Exterior Gateway Protocols (EGP, BGP)
- RTOS: Real-time Operating System. Scheduler in an RTOS is designed to provide a predictable (deterministic) execution pattern. Particularly of interest to embedded systems that must respond to a certain event within a strictly defined time (the deadline).
- variability in the item it takes to accept and complete a task is ‘jitter’.
- a ‘hard’ RTOS has less jitter than a ‘soft’ RTOS.
- chief design goal of an RTOS is a guarantee of a soft or hard performance category.
- if the OS can meet the deadline deterministically, it is a hard real-time OS.
- https://en.wikipedia.org/wiki/Real-time_operating_system
Big Picture of the Internet
Routing on the Internet is comprised of two parts:
- Internal, fine-grained portions managed by an IGP such as an Open Shortest Path First
- The interconnections of those autonomous systems (AS) via BGP.
Protocols
Networking protocols are rules that define how data is encoded and transmitted between different devices so that heterogeneous systems can communicate the “same language” with each other.
- https://www.comptia.org/content/guides/what-is-a-network-protocol
- https://www.cloudflare.com/learning/network-layer/what-is-a-protocol/
There are three primary types of protocols
Protocols are further subdivided by the layer of the OSI model in which they belong.
Routing Protocol
Specifies how routers communicate with each other, disseminating information that enables them to select routes between any two nodes on a network. Each router has a priori knowledge only of networks attached to it directly. There are three major classes of routing protocols:
- Interior gateway protocols type 1, link-state routing protocols, such as OSPF and IS-IS
- Interior gateway protocols type 2, distance-vector routing protocols, such as Routing Information Protocl, RIPv2, IGRP
- Exterior gateway protocols used on the Internet for exchanging routing information between autonomous systems, BGP, Path Vector Routing Protocol
Common Protocols
IP
Internet Protocol is a protocol for routing packets so that they can travel across networks to arrive at the proper destination. It is the principal communications protocol in the Internet protocol suite for relaying datagrams across network boundaries.
- The routing function enables internetworking and essentially establishes the internet.
- IP has the task of delivering packets from source to destination based solely on IP addresses in the packet headers which is tagged with both the source and destination address.
- Responsible for addressing hosts and routing datagrams, or packets, from a source host to a destination host across one or more IP networks.
- Provides an addressing system with TWO MAIN FUNCTIONS
- Host addressing and identification
- Packet routing
Packets
A segment of data with a Network Layer header that contains source ip and port socket, and destination ip and port socket, along with the payload.
- Building Internet Firewalls, anatomy of a packet (full text)
- https://www.techrepublic.com/article/exploring-the-anatomy-of-a-data-packet/

Difference between and IP address and an Ethernet Address?
An Ethernet Address, or MAC (Media Access Control), or physical address is ‘burned-in’ to the hardware. Comprised of 6 1 byte fields for a total of 48 bits. A component of the Ethernet Protocol.0
- A conceptual unique serial number for your NIC.
- This address is used only to direct packets from one device to another as data travels over the network.
- This address only travels to the next device, router, on the data path.
The IP Address is a 32 bit number (4 8-bit fields) that represent an individual machine and subnet of the network. The address is divided into a network and host address by the subnet mask. IP Addresses are used to move data between networks
TCP/IP
Also known as the Internet Protocol Suite as it is the set of protocols used in the Internet.
Transmission Control Protocol is a “reliable” or “guaranteed delivery” and flow control. Each packet sent has to be positively ack’d and arrive in the order that they are sent. Additional packets will not be sent until the current packet(s) have been sent and verified. It is used in systems where all of the data must be sent.
UDP
User Datagram Protocol is an “unreliable” or “not-guaranteed delivery” protocol. It is faster than TCP as there is no form of acknowledgment, flow control, or error correction and resending of data. It is used in systems where the loss of some of the data is tolerated by the application.
ICMP
Internet Control Message Protocol. Network protocol useful in IP network management and administration. ICMP is a required element of IP implementations. Designed not to carry data but information about the status of the network itself.
IGMP
Internet Group Management Protocol provides a way for multiple devices to share a single IPV4 address and thus receive the same data. It is used to setup multicasting allowing devices join multicast groups.
Multicast IPs are in the range 224.0.0.0 and 239.255.255.255.
IP multicasting means that one sender is sending data to multiple recipients but only sending a single copy. Similar to broadcast there are special addresses designated for multicast data. Multicast address space is 224.0.0.0/4 [224.0.0.0 – 239.255.255.255] (previously designated class D).
The difference between multicast and broadcast: multicast is more efficient as broadcast packets HAVE to be received by everyone on the local link. In multicast, the network card does not listen for multicast packets unless it has been told to do so.
- https://www.cloudflare.com/learning/network-layer/what-is-igmp/
- https://en.wikipedia.org/wiki/Internet_Group_Management_Protocol
- https://www.enterprisenetworkingplanet.com/standards-protocols/networking-101-understanding-multicast-routing/
ARP
Address Resolution Protocol is a layer 2 protocol used to map IP addresses to the MAC addresses of machines on the network and provides the mechanism for machines to communicate the ownership of IP addresses. ARP operates between layer 2 and layer 3 of the OSI model and exists solely to glue together IP and Ethernet network layers.
All hosts on the network maintain an ARP table to map IP addresses to MAC addresses. When sending a ping, the first thing that happens is the lookup of the MAC address. If it is not already in the ARP table, an ARP packet is broadcast to the network. The machine that has that address will respond with an ARP packet indicating that it has that IP and will include the MAC address of the machine.
A sending machine will send a broadcast Ethernet frame containing an ARP request to the entire network looking for the MAC address of a machine with a particular IP. All machines on the same network will receive this frame. If the machine receives the request that has the IP that is requested it will reply with the link layer address on which it will receive packets for that IP. Once the requester receives the response packet it will associate the target IP with the MAC address that it received, storing it in the arp cache. ($ arp; Will list the contents of the arp cache on a Linux system). The ARP reply is unicast.
- http://linux-ip.net/html/ether-arp.html#ether-arp-overview
- https://www.juniper.net/documentation/en_US/junose15.1/topics/concept/ip-arp-understanding.html
- https://www.techtarget.com/searchnetworking/definition/Address-Resolution-Protocol-ARP/
- https://www.geeksforgeeks.org/how-address-resolution-protocol-arp-works/
MAC Addresses
A MAC address is a low-level address of a unique network interface that is component of the Ethernet protocol. Packets sent on an Ethernet network have their source mac address compared against that of the receiving card. If they match the card it processes the packet, if not it discards the packet
IP protocol and MAC addresses work together, sort of, in that the IP protocol sits on a layer above MAC addressing. The IP protocol determines if the destination IP is on the same network, if so the destination can be reached directly and an ARP request is sent to determine the MAC of the destination IP address.
If the IP is NOT on the local network the IP protocol layer sends the packet to the gateway or router. The router then uses ARP to retrieve the MAC for the next hop (router) to send the packet to the destination IP. The target MAC is then written into the Ethernet header, and the packet sent.
OSI Model
The Open Systems Interconnect Model is a conceptual model used to describe the functions of a network.
A common mnemonic used to remember (from the bottom up) is, “please do not throw sausage pizza away“.
| Layer | Name | Mnemonic | Description |
| 7 | Application | Away | Interface with which applications interact with to communicate with the network. Specifies the shared protocols and interface methods used by hosts in a communications network. Used in both OSI and TCP/IP Protocols consist of HTTP, FTP, DNS, SMTP, SNMP, SSH |
| 6 | Presentation | Pizza | This layer formats and/or translates data for the Application layer. For example, in this layer data is converted to files (when downloading), or data is generified (broken up) for uploading and handed to lower layers. This layer is where encryption, decryption, authentication and compression occurs. |
| 5 | Session | Sausage | Maintains session for stateful connections. |
| 4 | Transport | Throw | Operates under two different communication paradigms, connected “sessions” and connectionless. This layer is responsible for managing communications between sender and receiver and establishing sessions. It enables multiple applications in layers above the Transport layer to establish client-server links to other networked devices. It provides flow control that insures packets are transmitted and received at a supportable rate. Ensures that packets transmitted have been received and assembled in the correct order. Provides acknowledgments to the sender upon reception of error-free packets. Requests re-transmission to sender when it receives a defective packet. Port numbers, both source and destination ports, are created and assigned at this layer. When the port is bound to an IP address a socket is created. Thus a socket is an IP + port #. The communication mechanism when establishing and managing connections between two devices at this layer is via sockets. Protocols – TCP – UDP – DCCP – SCTP https://www.sciencedirect.com/topics/computer-science/transport-layer-protocol |
| 3 | Network | Not | This layer adds a Network Layer header. and now we have a Packet. IP addressing happens in this layer, finding the best path in the network. The IP header is added. Routers and switches operate at this layer and provide switching and routing creating logical paths to transmit and control data flow. |
| 2 | Data Link | Do | Adds a Data Link header and we now have a Frame. Responsible for MAC addressing and error checking. The frame consists of a Link Layer Header and a Packet and is the final layer of encapsulation of data before it is serialized and sent across the network. The Frame contains a sequence of bits to indicate to the receiver the beginning and the end of the payload data within the stream of bits received. The receiver will ignore data it receives when beginning reads in the middle of a stream until it reads a new frame synchronization sequence. Examples: Ethernet Frames: A Data Link Packet on an Ethernet link. Each Ethernet Frame starts with an Ethernet Header (containing destination and source MAC addresses as the first two fields). Middle is the payload, may contain data of other protocols. The frame ends with a frame-check-sequence which is a 32-bit cyclic redundancy check Protocols – Ethernet – PPP (Point-to-point Protocol) – Fibre Channel Frames – V.42 modem Frames |
| 1 | Physical | Please | Actual data is transferred over the wire or wireless connection. Defines the electrical and physical specifications of the data connection. Defines the relationship between a device and a physical transmission medium. Defines transmission mode; simplex, half duplex, full duplex. Defines the network topology. Encoding into bits is done in this layer, analog or digital. Deals with raw data. Protocols – PON – OTN – IEEE 802.11 (wifi) – Bluetooth |
- https://www.techopedia.com/definition/24961/osi-protocols
- https://www.geeksforgeeks.org/layers-of-osi-model/
- https://www.imperva.com/learn/application-security/osi-model/
- https://www.softwaretestinghelp.com/osi-model-layers/
TCP/IP Model
This model is older and more simplified. Originally designed by the DoD
| OSI Model | TCP/IP | Description | TCP/IP Protocol Suite |
| Application Presentation Session | Application | Defines TCP/IP application protocols and how host programs interface with Transport Layer. | HTTP, SMTP, POP, SSH, DNS |
| Transport | Transport | – Defines a level of service and the status of the connections. – Permits devices on the source and destination hosts maintain session – Main protocols are TCP and UDP | TCP, UPD |
| Network | Internet | Packs data into packets, IP datagrams Defines Internet address scheme | ICMP IGMP |
| Network Data Link Physical | Network Access | Maps IP addresses to MAC addresses Encapsulates IP datagrams for transmission Routines for accessing physical networks | ARP Ethernet, Token Ring, ATM, Frame Relay |
Network FAQ
What is CRC?
Cyclic Redundancy Check. it is an error-detecting algorithm used to detect accidental changes to raw data. Data is assigned a check-value based on the remainder of a polynomial division of their contents. On retrieval, the calculation is repeated and the values compared. CRCs are implemented using binary math and as a result are relatively simple to implement and not expensive calculations.
What is Network Byte Order?
A standard “endianness” for determining MSB and LSB such that heterogeneous systems, specifically those that deal with networking, can unambiguously communicate with each other. TCP/IP network byte order is big-endian.
What is a routing table?
A table stored in a host or router that lists the routes to particular network destinations. Sometimes this include distances and other meta-data about the routes.
https://en.wikipedia.org/wiki/Routing_table
What is the loopback interface?
A special virtual network interface used for diagnostics and troubleshooting and to connect to servers running on the local machine. It exists so that, regardless of any hardware, applications running on the local machine can always connect to itself.
- https://en.wikipedia.org/wiki/Loopback#Virtual_network_interface
- https://en.wikipedia.org/wiki/Virtual_network_interface
- https://tldp.org/LDP/nag/node66.html
What is the broadcast address?
An address on the network that indicates that any information sent to it should be sent to all other addresses on the network. Usually a MAC address 0xffffffff. Used for protocols such as ARP and RIP (Routing Information Protocol)
https://en.wikipedia.org/wiki/Broadcast_address
What is the difference between unicast and broacast?
Unicast is a conversation between two hosts regardless of the routers between them, they are carrying on a private conversation. Broadcast traffic is a way of addressing all hosts in a given network range with a single destination IP address. Broadcast techniques are used at the Ethernet and IP layer so we are talking about Ethernet broadcasts, or IP broadcast. SMB and NetBIOS service location protocol, and DHCP.
What is the Basic Operation of DHCP?
- The client requesting and IP discovers a DHCP server by sending a DHCPDISCOVER message to the broadcast address for the network on UDP port 67. At this point, since the machine does not have any network configuration information it sends it to the “all ones” address, 255.255.255.255. This includes its MAC address and hostname
- A DHCP server on the network will respond with a DHCP OFFER message. The client may receive offers from multiple DHCP servers. The response indicates that the sending server has a lease that is available. The client will accept the first offer received.
- The client responds via a broadcast message with a DHCP Request message indicating that it accepts the offer and wants the IP address. Additional DHCP servers will also see this response and will rescind their offers.
- The DHCP server who’s offer was accepted will then send a DHCP Acknowledgement message. It can be either via unicast or broadcast. The message will include the IP being leased as well as other network configuration parameters
What is the difference between a VLAN and a VPN?
Virtual Private Network: method of simulating a private network that is operating on top of a larger network like the Internet.
VLAN: Virtual Local Area Network is a subcategory of a VPN. VPN constructs range from layer 1 – 3. A VLAN is purely layer 2. This allows you to group computers that are not necessarily connected to the same switch and make them act as if they were. You can relocate computers geographically and allow them to maintain the same connections and resources as before. You can also segment computers in a bigger local network into smaller groups, even if they are all connected to the same switch.
NAT Basics
Simply put, NAT changes the IP address in the IP header. It stands for Network Address Translation and allows the ability to translate one set of addresses to another, enabling traffic coming from a specific host to appear as though it is coming from another and to do it transparently.
Uses
- Translation of non-unique addresses into unique addresses when accessing the Internet. A NAT router at home to translate LAN ip ranges to WAN side valid IP allows machines to access the internet without having a publicly addressable IP.
- Translating addresses during an address re-organization of an organization.
- When simple TCP load sharing is required across many IP hosts, load balancing.
http://www.ciscopress.com/articles/article.asp?p=1725268
Encrypted UDP: DTLS, https://www.comparitech.com/net-admin/guide-udp-user-datagram-protocol/
TCP and UDP Packets
UDP
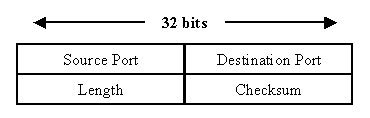
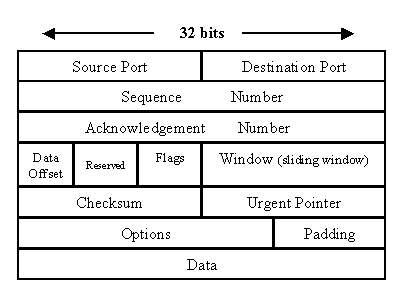
TCP
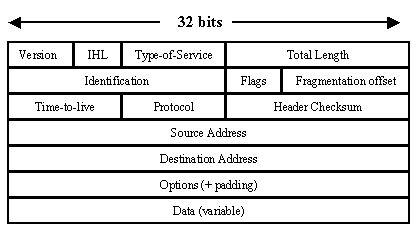
IP Packet
TCP 3-Way Handshake
The process by which a client and server establish a TCP connection with each other.
- SYN: The client, attempting to establish a connection with a server, chooses an initial sequence number and sends it in a packet with the synchronize bit set.
- SYN-ACK: The server reads the sequence number from the SYN packet and sends back a packet with both the acknowledge and synchronize bits set and an acknowledgement number set in the header. The acknowledgement number is the initial sequence number sent by the client +1. The sequence number returned in the syn-ack is different from that sent by the client in the initial syn request.
- ACK: The client receives the syn-ack message and returns an ack. This includes a packet with the acknowledge bit set and the the acknowledgement number as the received sequence number from the server +1. The synchronize bit is unset. At this point the connection is established.
Disconnection protocol is FIN, FIN-ACK, ACK.
https://afteracademy.com/blog/what-is-a-tcp-3-way-handshake-process
Network Types By Spatial Scope
- Nano
- BAN
- PAN
- LAN
- CAN
- MAN
- RAN
- WAN